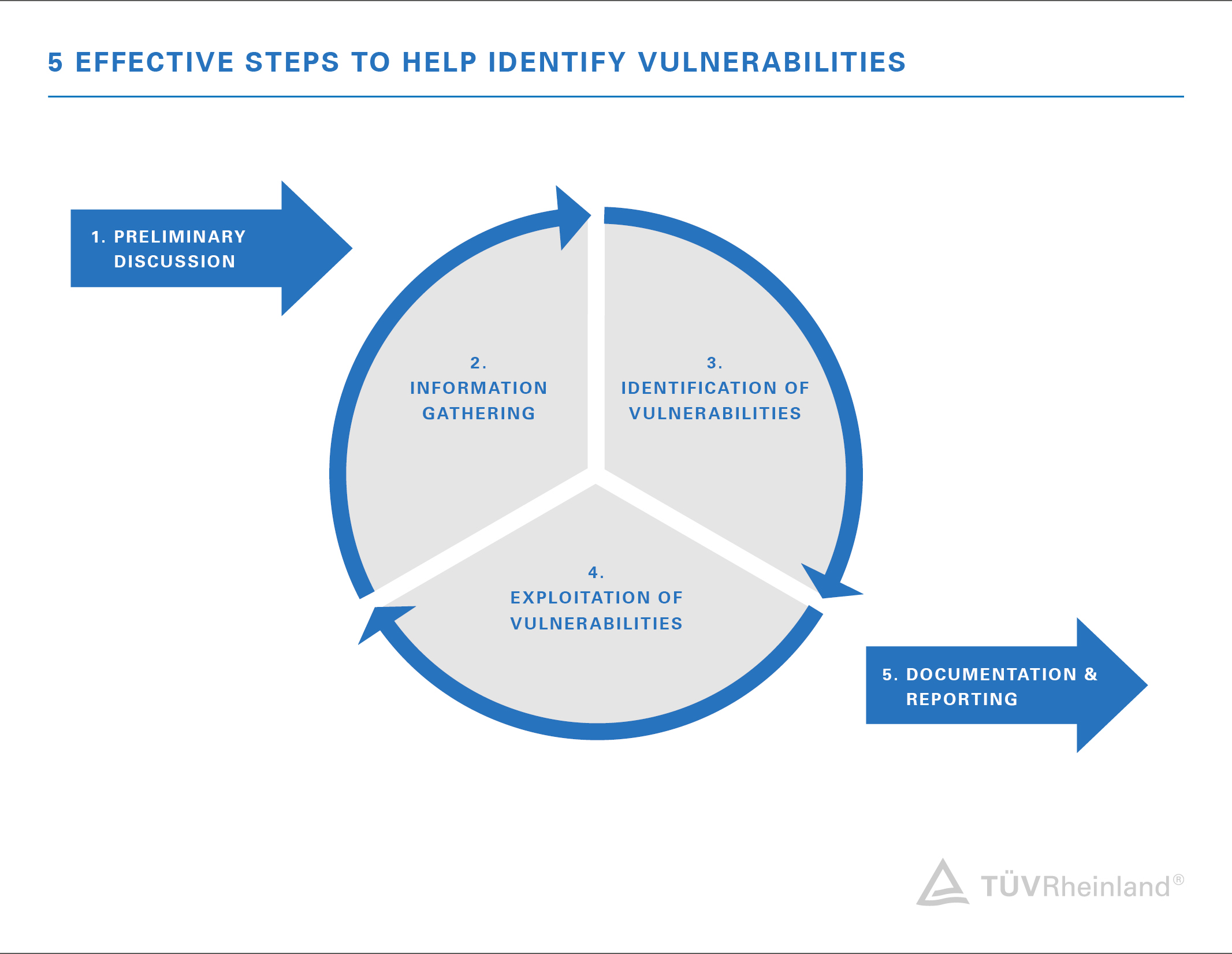
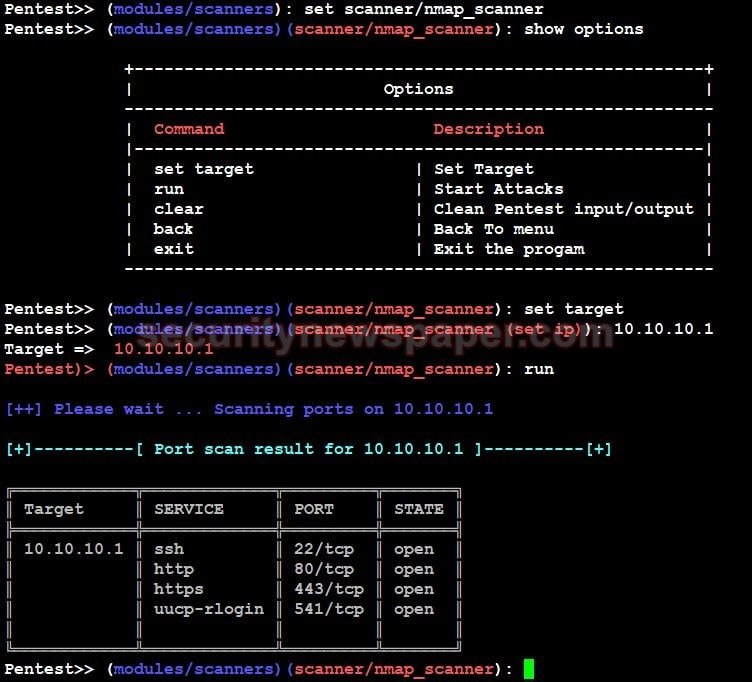
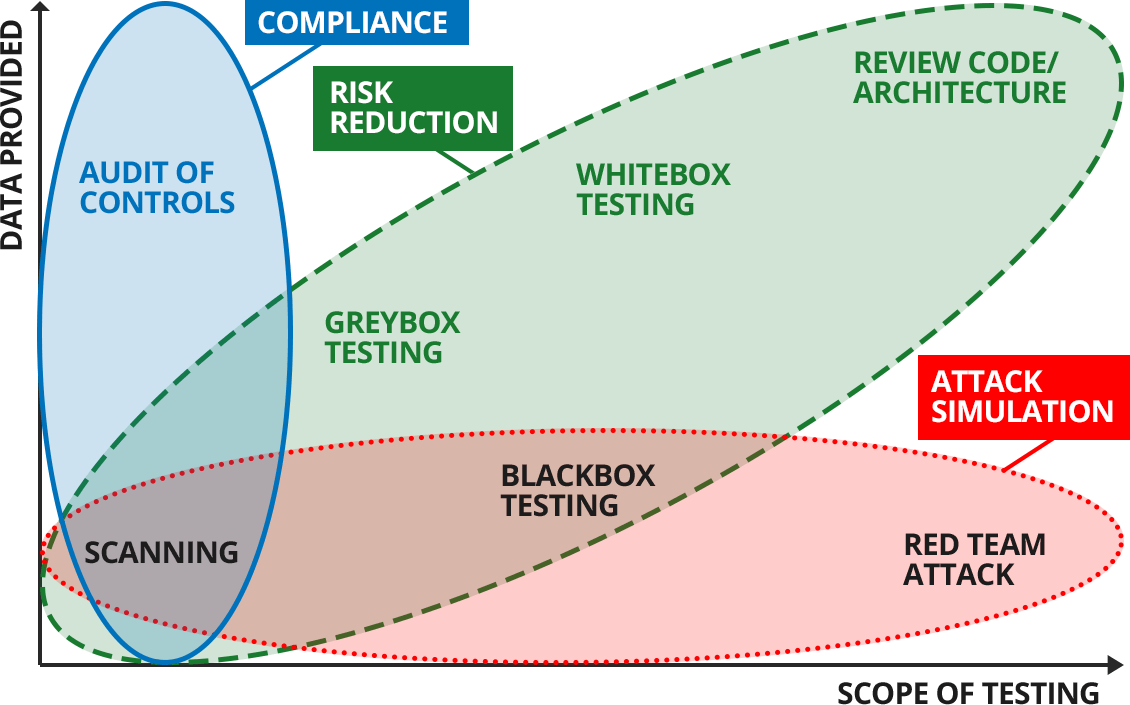
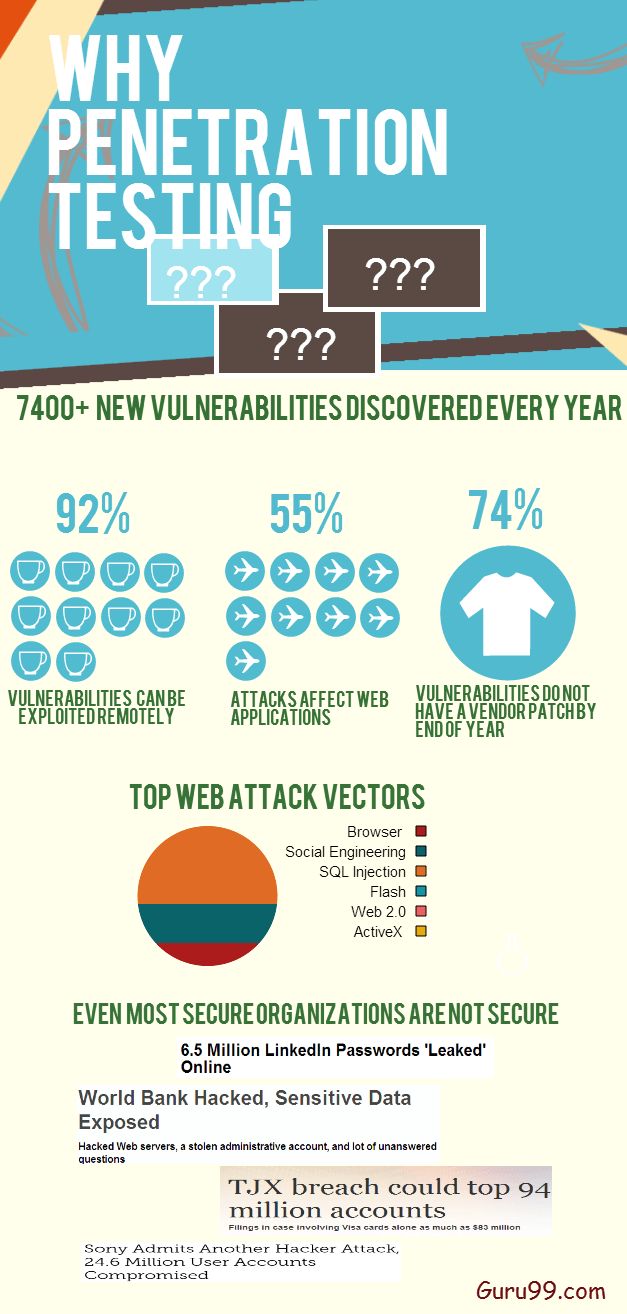
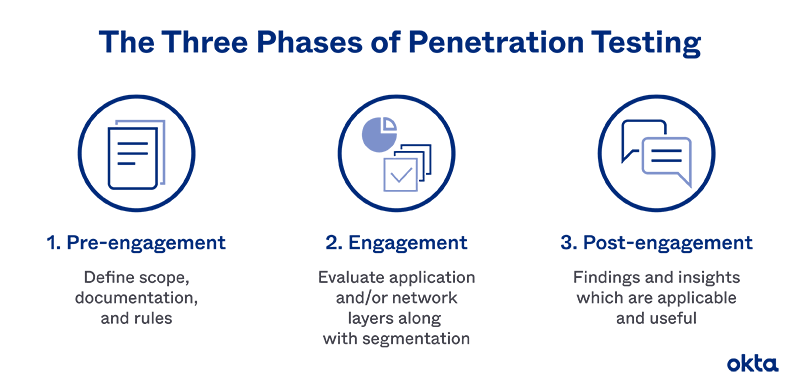
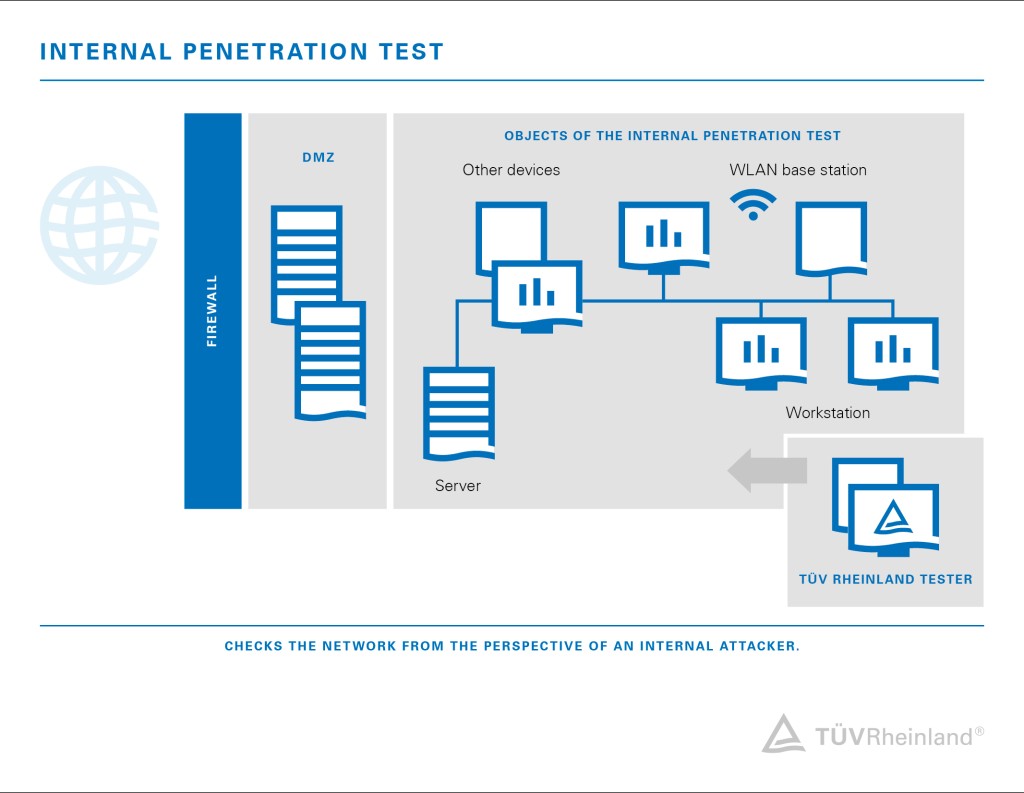
What Is Penetration Testing? Why Your Business Needs Penetration Testing? | Managed IT Services and Cyber Security Services Company - Teceze
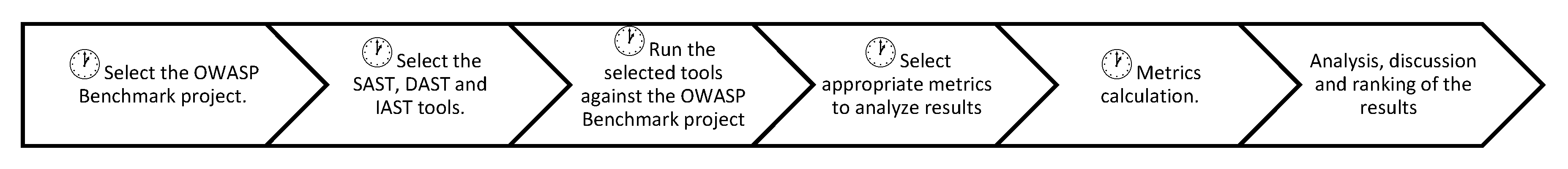
Applied Sciences | Free Full-Text | On Combining Static, Dynamic and Interactive Analysis Security Testing Tools to Improve OWASP Top Ten Security Vulnerability Detection in Web Applications | HTML

Cone penetration testing for extensive mapping of deeply buried Late Glacial coversand landscape paleotopography - Verhegge - 2021 - Geoarchaeology - Wiley Online Library


![PDF] An Overview of Penetration Testing | Semantic Scholar PDF] An Overview of Penetration Testing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/47ab031ed57e76b539cae466f376d745ccc18e28/4-Figure1-1.png)