![PDF] Needles in a Haystack: Mining Information from Public Dynamic Analysis Sandboxes for Malware Intelligence | Semantic Scholar PDF] Needles in a Haystack: Mining Information from Public Dynamic Analysis Sandboxes for Malware Intelligence | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e33f910829939417e6273e0e5e6b26887f6e1ce1/17-Table5-1.png)
PDF] Needles in a Haystack: Mining Information from Public Dynamic Analysis Sandboxes for Malware Intelligence | Semantic Scholar

Outline Infections 1) r57 shell 2) rogue software What Can We Do? 1) Seccheck 2) Virus total 3) Sandbox Prevention 1) Personal Software. - ppt download

Deep Malware Analysis - Architecture independent Malware Similarity Analysis with Joe Sandbox Class 3.0

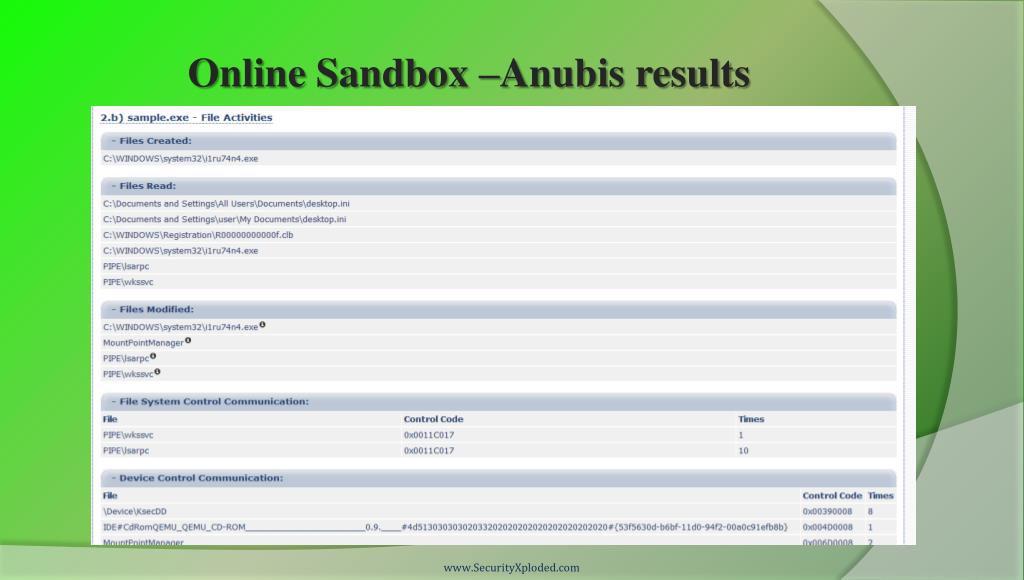
List of system activities from Anubis sandbox A number of input samples... | Download Scientific Diagram